- Mac Os X Sierra Image
- Mac Os X Server For Sierra Leone
- Mac Os X Sierra Hackintosh
- Mac Os Sierra Download
- Mac Os X Sierra Requirements
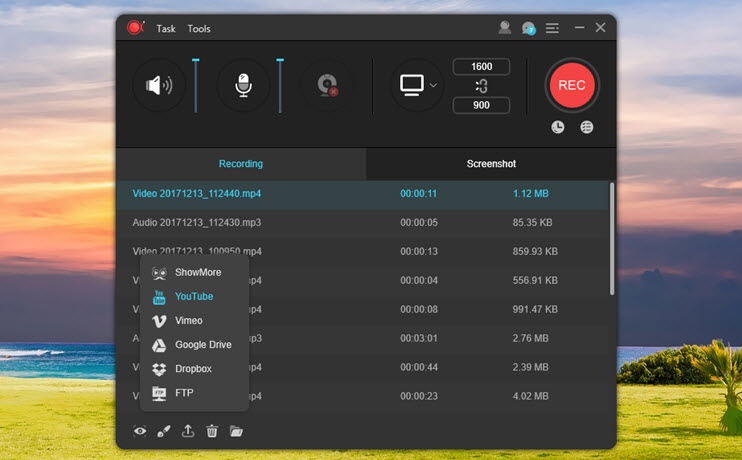
- Ftp Server Macos High Sierra
Mac OS X & macOS names. As you can see from the list above, with the exception of the first OS X beta, all versions of the Mac operating system from 2001 to 2012 were all named after big cats. Apple created the XQuartz project as a community effort to further develop and support X11 on Mac. The XQuartz project was originally based on the version of X11 included in Mac OS X v10.5. There have since been multiple releases of XQuartz with fixes, support for new features, and additional refinements to the X11 experience.
We all know VMWare start to supporting Mac OS X as VM on latest ESXi hypervisor releases. According to Apple licensing policies, VMware only supports the virtualization of Apple Mac OS X 10.10 (Yosemite) client or server, Apple Mac OS X 10.11 (El Capitan) client or server, Mac OS X 10.9 (Mavericks) client or server, Mac OS X 10.8 (Mountain Lion) client or server, Mac OS X 10.7 (Lion) client or server, 10.6 (Snow Leopard) server and 10.5 (Leopard) server.
The End User License Agreement (EULA) for Apple Mac OS X legally and explicitly binds the installation and running of the operating system to Apple-labeled computers only. Mac OS X 10.5 Leopard Server, 10.6 Snow Leopard Server, 10.7 Lion client or server, 10.8 Mountain Lion client or server and 10.9 Mavericks client or server are fully supported on VMware Fusion while running on supported Apple hardware.
In this HOWTO, provided the steps to create an Mac OS X 10.9 Mavericks as a VM in ESXi 6.0 Host for a test case scenario. Before deployment, you must read EULA for Apple Mac OS X license, given link at the end of this HOWTO.
8 Steps total
Step 1: Steps to do
1. VMware ESXi 6.0 doesn't support OS X out of the box. So, the first thing you need to do is to customise the hypervisor layer by executing an Unlocker script by insanelymac.com. You will need to register on the site in order to download the Unlocker tool.
2.You need to enable SSH server service on your ESXi host. In order to do that, login to the host using VMware vSphere Client and navigate to Configuration->Security Profile. From here click on Properties in the upper right corner where it says Services. The dialog Services Properties should appear and from here you can click on SSH->Options and choose Start and Stop with host. Click Start and then close all the open dialogs.
3.Transfer the Unlocker-files to the host using any SFTP client. Make sure you extract the files somewhere on your client before transfer and connect to the ESXi host using the user root. Once connected navigate to /vmfs/volumes/datastore/, replacing datastore with your actual datastore name. Create a new folder (mkdir) called tools and transfer your unlockerXXX directory.
4.Now cd into the uploaded directory and ensure the ESXi scripts have execute permissions by running chmod +x esxi-install.sh. Now run ./esxi-install.sh in order to install the Unlocker.
5. Reboot ESXi host.
Step 2: Download and create the bootable OS X Sierra ISO
Grab the Sierra installer app from the Apple App Store. Note, you need a Genuine Mac machine in order to download and convert the Sierra installation disk. Once downloaded, minimize or close the installer.
Open the terminal and run the below command one after another.
# Mount the installer image
hdiutil attach /Applications/Install macOS Sierra.app/Contents/SharedSupport/InstallESD.dmg -noverify -nobrowse -mountpoint /Volumes/install_app
# Create the Sierra Blank ISO Image of 7316mb with a Single Partition – Apple Partition Map
hdiutil create -o /tmp/Sierra.cdr -size 7316m -layout SPUD -fs HFS+J
# Mount the Sierra Blank ISO Image
hdiutil attach /tmp/Sierra.cdr.dmg -noverify -nobrowse -mountpoint /Volumes/install_build
# Restore the Base System into the Sierra Blank ISO Image
asr restore -source /Volumes/install_app/BaseSystem.dmg -target /Volumes/install_build -noprompt -noverify -erase
# Remove Package link and replace with actual files
rm /Volumes/OS X Base System/System/Installation/Packages cp -rp /Volumes/install_app/Packages /Volumes/OS X Base System/System/Installation/ Visual composer for mac download.
# Copy Sierra installer dependencies
cp -rp /Volumes/install_app/BaseSystem.chunklist /Volumes/OS X Base System/BaseSystem.chunklist cp -rp /Volumes/install_app/BaseSystem.dmg /Volumes/OS X Base System/BaseSystem.dmg
# Unmount the installer image
hdiutil detach /Volumes/install_app
# Unmount the Sierra ISO Image
hdiutil detach /Volumes/OS X Base System/
# Convert the Sierra ISO Image to ISO/CD master (Optional)
hdiutil convert /tmp/ElCapitan.cdr.dmg -format UDTO -o /tmp/ElCapitan.iso
# Detach the volumes
hdiutil detach /Volumes/install_app
hdiutil detach /Volumes/OS X Base System/
hdiutil convert /tmp/Sierra.cdr.dmg -format UDTO -o /tmp/Sierra.iso
# Rename the Sierra ISO Image and move it to the desktop
mv /tmp/Sierra.iso.cdr ~/Desktop/Sierra.iso
Note : Once done it should have created a file called Sierra.iso on your desktop.
Step 3: Create a virtual Mac OS X VM
The next step should be fairly simple if you have used ESXi before. As usual open your datastore and transfer the iso to wherever you normally store your installation files.
1. Create a New VM
2.Select Typical and you should be able to select Other and then Apple Mac OS X 10.10 (64-bit). Complete the wizard, mount the ISO and install Mac OS X as usual.
Step 4: Mac OS X Installation steps - Language selection
Choose desired language once you see the welcome screen
Step 5: Mac OS X Installation step - Formatting the hard drive.
Also note that you must format the hard drive using the disk utility before it will be visible in the install wizard.
Step 6: Mac OS X Installation step - Choose Virtual disk and erase the partition
Choose Virtual disk and erase the partition
Step 7: Mac OS X Installation step - Choose Virtual disk and erase the partition 2
Give a name and click 'Erase'.
Click 'Continue' button on the next consecutive screen, choose the Virtual HDD which is created and proceed the installation with on-screen instructions
Step 8: Configure Mac OS X after install
It's very important to install the VMware Tools as soon as possible after the install has finished. Without it Mac OS X might not awake from sleep and in general be very unreliable.
Very Important : I also recommend to turn off sleep and the screensaver in settings as these may cause issues.
Finally, reboot and start enjoying your virtual Mac on non-Apple hardware.
You may also wish to read the software license agreement for Mac OS Sierra provided in the References section.
As said, using Apple Mac OS X as a VM on vmware environment is subject to apple EULA. VMWare recommend to use VMWare fusion for installing Mac OS X 10.9 Mavericks.
References
- Apple EULA
- Installing OS X 10.9 Mavericks as a guest operating system in VMware Fusion (2056603)
- Virtualizing Apple Mac OS X (1000131)
3 Comments
- Anaheimthelaz Apr 25, 2017 at 03:30pm
Tried this - didn't work for me. Never made it to install screen. Did I miss anything that says this is for Apple hardware only? There's a ton of these guides out there that are generally the same - to my knowledge those that include the unlocker step are for non-Apple platforms.
- AnaheimMaster RX Sep 25, 2018 at 09:32pm
Hello, it worked for me. with the process I was able to create an ISO for Yosemite macOS. however it does not work for me to create an iso of macOS Mojave. you know if the creation process has changed or if it's just mojave can not be used with VM
- HabaneroGopal (Vembu) Sep 26, 2018 at 06:03am
Master RX
Yes, We tried with Yosemite and Sierra macOS only, since it was the latest that time. We have not tried with Mojave yet, and not sure process has changed.
We have a lot of customers who use their Mac mini as a VPN server. This works great when you need an IP address in the US, or a secure internet connection on the road, or a number of other reasons. When Apple released Lion, they changed the setup a bit so we wrote a tutorial. This continued in Mountain Lion and Mavericks, Yosemite, El Capitan, and remains the case in Sierra. By default, Sierra Server VPN will distribute IP addresses in the same range the Mac itself uses. This doesn't work well in a facility like MacStadium where each Mac mini has a static WAN IP address.
We asked Rusty Ross to help us put together a tutorial that will help MacStadium customers setup their Mac minis to serve as VPNs. He's broken it down in a few parts so be sure to take the steps that are best for your situation:
PART I: VLAN and DNS
PART II: Internet Routing (OPTIONAL)
PART III: VPN
Mac Os X Sierra Image
PART IV: Client Setup
If you are simply looking to enable VPN service on your macOS Server for secure connection(s) between your server and client(s), you can skip PART II. That's right: you can jump straight from PART I to PART III. The procedures discussed in PART II are intended for those who are looking to route internet traffic from their VPN clients over the VPN and out to the internet via their server's public internet connection at Macminicolo.
Also, it should be mentioned that server administration (particularly at the command line level) can be tricky. If you do proceed beyond this point, which shall be exclusively at your own risk, then please proceed carefully, and as always, don't ever proceed without a backup of your server and other irreplaceable data.
Still here? Okay, let's get started.
PART I: VLAN and DNS
First, let's set up a VLAN.
In System Preferences, go to Network, and choose 'Manage Virtual Interfaces…'
Then choose 'New VLAN…'
Let's just name our VLAN something like 'LAN', and all other defaults here should be fine:
After pressing 'Create', you'll see this:
After pressing 'Done', you'll be able to enter network info for your new VLAN. Make sure to choose 'Manually' for 'Configure IPv4', and set the IP Address, Subnet Mask, and Router as shown below.
(Advanced: We'll be using a 10.0.0.1 private IP for the server and 10.0.0.0/24 private network in this walkthrough, but note that the technique documented here will work with any private IP addressing scheme. To accomplish that, you'd substitute that alternate network info here, as well as a few other places further along in this walkthrough.)
After pressing 'Apply', you should see an something like this, indicating that your newly-created VLAN is active:
Nice work. Now, let's get basic DNS up and running. Launch Server.app, and click on the 'DNS' section of the sidebar, under 'Advanced':
All DNS defaults in Server.app should be fine, so let's switch DNS service on:
Great. Now, once again, if you are NOT interested in routing public internet traffic from your VPN client(s) over the VPN and out to the internet via your server's public internet connection at Macminicolo, you should SKIP from here to PART III.
PART II: Internet Routing (OPTIONAL)
So far, so good. Now things get a little trickier, as we need to dive into the command line a bit to get NAT and routing set up. First, we'll need to edit two privileged text files, so we are going use a command line text editor called nano. Breathe easy, we've got each other's backs here, and we will take this step by step.
As we proceed, it is important to remember that in the command line, typos aren't the least bit welcome, and also, uppercase/lowercase needs to match exactly, so it is extremely important to enter text into Terminal.app exactly as it is described here.
One additional (but important!) point: The quotation marks used here in terminal commands are 'straight' quotes. Some web browsers and text editors may automatically convert these marks to smart (curly) quotes, particularly when copying and pasting. It's important to use straight quotes when entering the commands from this tutorial in Terminal.app.
Mac Os X Server For Sierra Leone
Okay? Let's forge ahead.
Launch Terminal.app:
Inside the terminal window that appears, enter the following command (as a single line), and press return:
sudo nano /etc/pf.anchors/com.appleYou'll be prompted for your password, and if you've not used sudo on this Mac in the past, you may see a warning about using sudo, which is fine. Enter your password (you wont see the cursor move while you type your password) and press return:
Upon doing this, you should expect to see the following text file open inside of nano, our friendly command line text editor:
Okay, we are now going to add three custom lines to this document. Red arrows in the picture below indicate where these lines should go. To move the cursor into the correct place to add these lines, simply use the arrow keys on your keyboard.
The three lines you'll be adding are:
nat-anchor '100.customNATRules/*'rdr-anchor '100.customNATRules/*'
load anchor '100.customNATRules' from
'/etc/pf.anchors/customNATRules'
Great. Now we need to tell nano to save the changes you made to this text file. This will be a three step process, and we'll take it one step at a time.
First you'll press the 'control' key and the 'X' key simultaneously (that's right, 'control-X') to tell nano you are done editing. Upon doing so, you will see this:
Now press the 'Y' key to let nano know that, yes indeed, you do want to save changes:
And finally, nano is already suggesting the proper location to save the file you edited, so simply press return to accept its suggestion:
Well done! You are back where you started, having edited a text file in nano.
Since you are now a nano expert, let's use it once more, this time to create an entirely new text file. Start nano up again as follows:
sudo nano /etc/pf.anchors/customNATRulesUpon entering the command above and pressing return, you will be reunited with your friend nano, now editing a new text file which, thus far, contains no text:
We are simply going to add two lines of text here:

pass from {lo0, 10.0.0.0/24} to any keep state
(Advanced: If you are using private IP addressing other than 10.0.0.0/24, you should customize these two lines to match your chosen network.)
And now that these two lines have been added, well, you know the drill, the old three-step save: 'control-X', then 'Y', and then press return.
Again, that's 'control-X':
Then 'Y':
And then press return:
Excellent. Though nano has served us well, we won't need to use it again during this tutorial.
Now, just a couple more commands in Terminal.app, and we'll be done with the command line altogether.
Enter this command (as a single line) into your Terminal.app window and press return:
sudo pfctl -f /etc/pf.confYou'll get some feedback on this one from the Terminal, all of which you can safely ignore.
Next, enter this command (as a single line) into your Terminal.app window and press return:
echo 'net.inet.ip.forwarding=1' | sudo tee -a/etc/sysctl.conf
The Terminal should respond with 'net.inet.ip.forwarding=1', which is what we want.
And finally, enter these five commands (each one as a single line, pressing return after each one) into your Terminal.app window:
sudo cp/System/Library/LaunchDaemons/com.apple.pfctl.plist
/Library/LaunchDaemons/net.macminicolo.pfctl.plist
sudo sed -i ' 's/com.apple.pfctl/net.macminicolo.pfctl/'
/Library/LaunchDaemons/net.macminicolo.pfctl.plist
sudo sed -i ' 's/>-f-e/Library/LaunchDaemons/net.macminicolo.pfctl.plist
sudo sed -i ' '/pf.conf/d'
/Library/LaunchDaemons/net.macminicolo.pfctl.plist
sudo launchctl load -w
/Library/LaunchDaemons/net.macminicolo.pfctl.plist
Well done. You can now close your Terminal.app window entirely.
Okay, you have now set up NAT and routing for your private network. The last piece of the puzzle on the server will be to configure and enable VPN service.
Before you proceed, though: RESTART your server now. (We'll wait…)
Now that you have restarted your server, let's continue.
PART III: VPN
Mac Os X Sierra Hackintosh
Whether or not you have just completed Part II or skipped to this point straight from Part I, rest assured that everyone is welcome here in Part III.
First, open Server.app and click on the 'VPN' section of the sidebar:
Mac Os Sierra Download
Several default settings here are already in place as we'd want them, so we'll just edit a few.Enter your Shared Secret as desired:
Now press 'Edit…' next to DNS Settings. You will likely see the Macminicolo DNS IP addresses here, which is NOT what we want in this particular place:
Instead, change this to 10.0.0.1 as follows:
(Advanced: If you are using an alternate private network, customize the above appropriately.)

Press 'OK' and we're back here:
Now press 'Edit…' next to Client Addresses, and enter settings as pictured below:
(Advanced: If you are using an alternate private network, or have different needs in terms of address pool size, customize appropriately.)Press 'OK' and once again, we are back here:
..and should be all set to go. Switch the VPN service on:
Brilliant. Wait about 30 seconds for the VPN service to become fully active, and your Mac mini server should now be ready to serve VPN clients and (optionally, if you completed Part II) route their public internet traffic over its connection.
PART IV: Client Setup
Now that your server's VPN is configured, enabled, and (optionally) ready to route public internet traffic for its clients, you may want a little guidance on how best to configure a client.
Let's set up a Sierra client as an example.
In System Preferences, go to Network, and press the '+' in the lower-lefthand corner:
Choose 'VPN', make sure you are using 'L2TP over IPSec', and give your service a name:
Mac Os X Sierra Requirements
Press 'Create', and then make sure your new VPN is selected in the sidebar on the left, so you can edit its details on the right:
As shown above, enter the IP address or DNS name for your server in the 'Server Address' field. In the 'Account Name' field, enter the username for the account on the server that you want to use to log in from the client.

Press 'Authentication Settings…' and you'll see this:
pass from {lo0, 10.0.0.0/24} to any keep state
(Advanced: If you are using private IP addressing other than 10.0.0.0/24, you should customize these two lines to match your chosen network.)
And now that these two lines have been added, well, you know the drill, the old three-step save: 'control-X', then 'Y', and then press return.
Again, that's 'control-X':
Then 'Y':
And then press return:
Excellent. Though nano has served us well, we won't need to use it again during this tutorial.
Now, just a couple more commands in Terminal.app, and we'll be done with the command line altogether.
Enter this command (as a single line) into your Terminal.app window and press return:
sudo pfctl -f /etc/pf.confYou'll get some feedback on this one from the Terminal, all of which you can safely ignore.
Next, enter this command (as a single line) into your Terminal.app window and press return:
echo 'net.inet.ip.forwarding=1' | sudo tee -a/etc/sysctl.conf
The Terminal should respond with 'net.inet.ip.forwarding=1', which is what we want.
And finally, enter these five commands (each one as a single line, pressing return after each one) into your Terminal.app window:
sudo cp/System/Library/LaunchDaemons/com.apple.pfctl.plist
/Library/LaunchDaemons/net.macminicolo.pfctl.plist
sudo sed -i ' 's/com.apple.pfctl/net.macminicolo.pfctl/'
/Library/LaunchDaemons/net.macminicolo.pfctl.plist
sudo sed -i ' 's/>-f-e/Library/LaunchDaemons/net.macminicolo.pfctl.plist
sudo sed -i ' '/pf.conf/d'
/Library/LaunchDaemons/net.macminicolo.pfctl.plist
sudo launchctl load -w
/Library/LaunchDaemons/net.macminicolo.pfctl.plist
Well done. You can now close your Terminal.app window entirely.
Okay, you have now set up NAT and routing for your private network. The last piece of the puzzle on the server will be to configure and enable VPN service.
Before you proceed, though: RESTART your server now. (We'll wait…)
Now that you have restarted your server, let's continue.
PART III: VPN
Mac Os X Sierra Hackintosh
Whether or not you have just completed Part II or skipped to this point straight from Part I, rest assured that everyone is welcome here in Part III.
First, open Server.app and click on the 'VPN' section of the sidebar:
Mac Os Sierra Download
Several default settings here are already in place as we'd want them, so we'll just edit a few.Enter your Shared Secret as desired:
Now press 'Edit…' next to DNS Settings. You will likely see the Macminicolo DNS IP addresses here, which is NOT what we want in this particular place:
Instead, change this to 10.0.0.1 as follows:
(Advanced: If you are using an alternate private network, customize the above appropriately.)
Press 'OK' and we're back here:
Now press 'Edit…' next to Client Addresses, and enter settings as pictured below:
(Advanced: If you are using an alternate private network, or have different needs in terms of address pool size, customize appropriately.)Press 'OK' and once again, we are back here:
..and should be all set to go. Switch the VPN service on:
Brilliant. Wait about 30 seconds for the VPN service to become fully active, and your Mac mini server should now be ready to serve VPN clients and (optionally, if you completed Part II) route their public internet traffic over its connection.
PART IV: Client Setup
Now that your server's VPN is configured, enabled, and (optionally) ready to route public internet traffic for its clients, you may want a little guidance on how best to configure a client.
Let's set up a Sierra client as an example.
In System Preferences, go to Network, and press the '+' in the lower-lefthand corner:
Choose 'VPN', make sure you are using 'L2TP over IPSec', and give your service a name:
Mac Os X Sierra Requirements
Press 'Create', and then make sure your new VPN is selected in the sidebar on the left, so you can edit its details on the right:
As shown above, enter the IP address or DNS name for your server in the 'Server Address' field. In the 'Account Name' field, enter the username for the account on the server that you want to use to log in from the client.
Press 'Authentication Settings…' and you'll see this:
Enter the Password for the account you just specified, and the Shared Secret exactly as you set it up on the server.
Press 'OK', and you are back to:
Now press 'Advanced…' and you should see this panel:
If you chose to complete optional 'Part II: Internet Routing' section earlier:
Then you should check the option to 'Send all traffic over VPN connection' so that your client will, um, send all its traffic (including public internet-bound traffic) over the VPN when the VPN connection is active.
Otherwise, if you skipped the optional 'Part II: Internet Routing' section, make sure to un-check 'Send all traffic over VPN connection' (unlike the picture above).
Press 'OK', and you are back to:
Press 'Apply' to save changes.
And now your client should be ready to connect to your server's VPN.
Just press 'Connect' when you want make this happen.
Well done.
As I mentioned, this tutorial came from Rusty Ross (@ConsultantRR), a great hands-on consultant that works with a bunch of happy MacStadium customers on a wide range of topics, including setup, migration, troubleshooting, maintenance, networking, strategic planning, and creative thinking. He's available for a quick-fix, a specific project, or a longer-term relationship.
Ftp Server Macos High Sierra
Until next year..
